Stuxnet Malware Analysis with Ghidra
- Esky Man
- Jun 25, 2023
- 2 min read
I've been watching quite a few video courses online about using open-source Ghidra which is pre-installed on Remnux to analyse various malware samples in my home lab.
Let me begin by showing you my home lab:

Ive got a desk with my 2015 27" imac powering my day to day computer usage, the mac has an i5 with 32GB of ram and 2TB SSD installed. Ive attached two monitors to the imac for a 3 screen setup, the far right monitor being in portrait, which is super handy.
I have Virtual Box running with various operating systems installed, including Windows 10, Windows 11 Ghost Spectre, Kali Linux, Kali Purple and Remnux.
Under the desk I have a custom built Windows PC which is a Ryzen 7, 32GB DDR4 Ram, 2TB SSD and an Nvidia 3060 GPU. My OS of choice on this machine is Windows 10 Ghost Spectre, but I also have Virtual Box installed with a couple of different Kali installs and another Win 10 VM.
Behind this setup I have a very untidy foldable table with a soldering iron station, loads of spare drives and USB drives, 2 hard drive cloners and a bunch of hand tools. I mainly use this table to solder Arduino boards that I mess about with. I used to solder, flash and pre wire the KL25Z Freedom boards for use in digital pinball machines. Ive also got a bunch of parts im playing around with to create bad USB's.
Anyway enough of my home lab, let's move on to the good stuff.
Here I have Ghidra open on Remnux with the infamous Stuxnet virus imported in to a new project. Im going to start writing down my findings and recording the reverse engineering of this malware package.
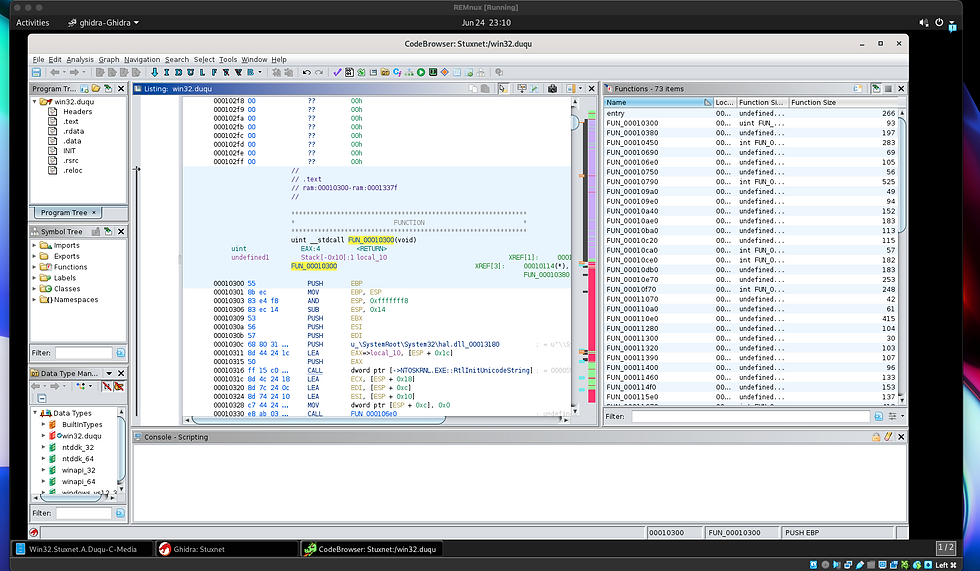
Having a look through the code I am able to tell this is probably disassembled x86 assembly code.
One of the first blocks of code sets up the function prologue I believe by pushing the value of the base pointer (EBP) onto the stack and then copying the current stack pointer (ESP) into the base pointer. It aligns the stack by ANDing ESP with 0xffffffff8 and subtracts 0x14 bytes from the ESP to allocate space for local variables. EBX, EDI and ESI values are pushed on to the stack and saved for later use.

Next the code is pushing presumably a string to a file path on to the stack. Then it loads the address of a local variable (local_10) into EAX by adding an offset to ESP. The code calls a function at the address stored in the dword pointer (->NTOSKRNL.EXE::RtIInitUnicodeString).
NTOSKRNL.exe is a system process, it's also known as the Windows NT OS System Kernel Executable.

So far im just at the beginning of my malware analysis journey. I should have probably started with an easier malware sample I know, but for now I will keep digging.


