Let's Attack My Own Server with a Denial of Service !
- Esky Man
- Sep 23, 2023
- 2 min read
Updated: Jan 27, 2024
In today's article I am going to demonstrate how I initiated a denial of service attack on my own Windows 2016 Server VM in order to learn more about DOS attacks and more importantly how to protect against them.
To begin with let me set the scene. I have three VMs setup in an Azure lab. A Windows Server install (which will be the victim machine), a Kali Linux VM (my attack machine) and a third Word Press setup which will be used in a later experiment. All three VMs sit within an Azure VM lab.
So before we begin the attack let's ensure that both the attack machine and the victim machine are on the same network. My Windows server resides at 10.10.10.1 so I set my Kali machine to 10.10.10.4

Next we need to misconfigure the Windows machine to allow ICMP packets:
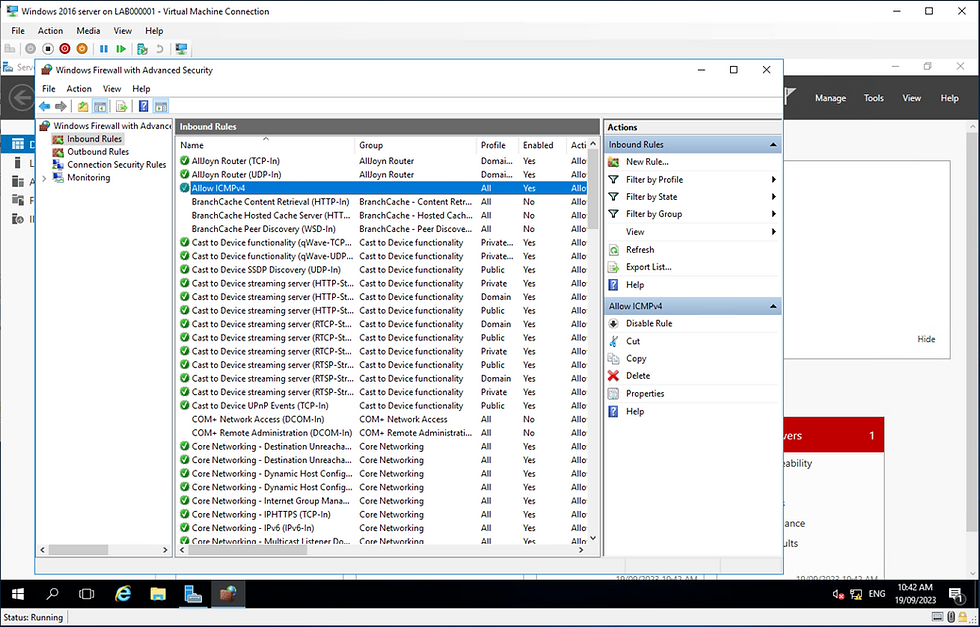
Next let's test our configurations by pinging the kali to win machine and visi-versa:


Ok so wee have connectivity between the two VM's and the Windows Server has been misconfigured to allow ICMPv4 packets. LET THE FUN BEGIN!
I am going to use Hping3 which is a DOS tool built in to Kali, I am going to initiate the following command :
sudo hping3 -c 10000 -S 10.10.10.1 --flood

This command will send 10000 packets to the Windows machine, if we open the Windows resources tab we can see that BEFORE I attack the server the CPU resources are sitting comfortably at around 2%:

Let's initiate the denial of service attack and see what happens to the Windows CPU:

We can see the CPU reaches around 89%, not enough for a total denial of service. Let's ramp up the attack with more packets and make the machine crash:

You can see that after this SYN flood attack, where I sent 50,000 packets, the Windows server maxed out its CPU resources and shortly afterwards it crashed. A successful denial of service attack all done with one simple command. Ok well you might be thinking this is all very good but how often would a Windows server be misconfigured in this way? Is this realistic? The short answer is YES. Many servers have misconfigurations and there are millions of web servers that are unpatched running old software that could allow attacks.


