Hunting malware by hand, identifying persistence and removing it from a Win10 VM.
- Esky Man
- Aug 5, 2023
- 3 min read
I was given the task of hunting for some persistent malware on an Azure VM. The task was to identify the malware, discover how it worked, how it maintained persistence and then remove it from the system, all by hand, no anti virus software allowed ! A good test for any infosec student. The only tools I HAD to use was Splunk. The task included being specific with the commands I chose to use in Splunk and I had to write them down.
I was able to quickly identify and locate a suspicious file in the Task Manager, called 23ffgg.exe. Having a look at the processes properties I can see it is being launched from a location on the local disk. I tried ending the process, deleting the file from it's execution location on disk and rebooting.... The malware came back after rebooting.

I used to Splunk to search for any registry keys being added to the system:
EventCode=4657 AND Object_Name="*Software\\Microsoft\\Windows\\CurrentVersion*"
The search confirmed a registry key was added for the file "23ffgg.exe" in:
HKEY_CURRENT_USER\Software\Microsoft\Windows\CurrentVersion\

I ended the malicious process again from task manager and deleted the file from disk. Next I ran regedit from the command line (because that is just the way I love doing it!) and navigated to the location in the registry identified in Splunk.
I investigated the following registry locations just to be absolutely sure I am aware of all files that are being executed on Windows startup :
HKEY_CURRENT_USER\Software\Microsoft\Windows\CurrentVersion\Run HKEY_CURRENT_USER\Software\Microsoft\Windows\CurrentVersion\RunOnce HKEY_LOCAL_MACHINE\Software\Microsoft\Windows\CurrentVersion\Run HKEY_LOCAL_MACHINE\Software\Microsoft\Windows\CurrentVersion\RunOnce
I located the registry key called “threat” in HKEY_CURRENT_USER\Software\Microsoft\Windows\CurrentVersion\Run
The malicious keys Value Data is C:\Windows\app\23ffgg.exe
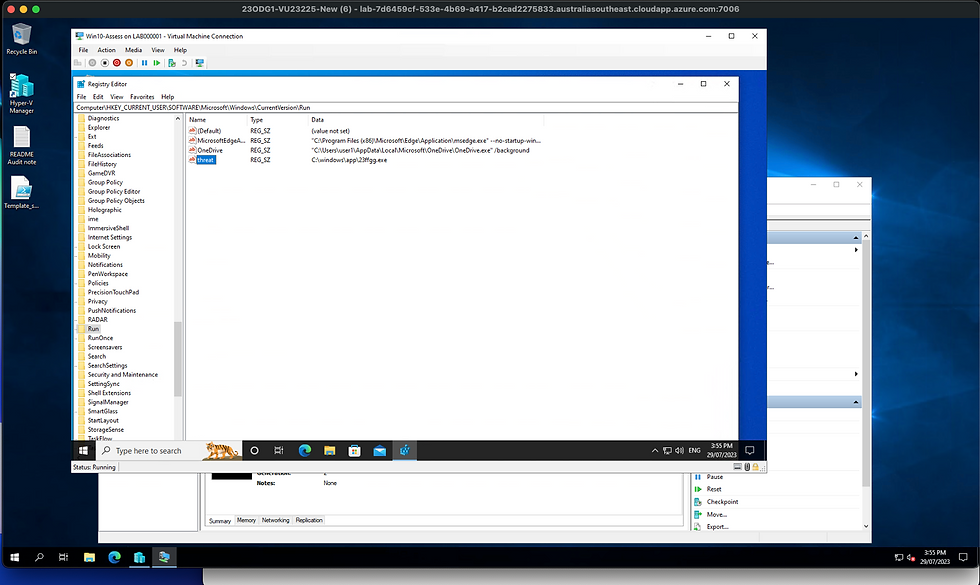
I deleted the key and then moved on to checking if anything was being run from startup folders using Splunk:
Object_Name="C:\\Users\\User1\\AppData\\Roaming\\Microsoft\\Windows\\Start Menu\\Programs\\Startup\\*"
I also checked the folders manually just to double check, I turned on hidden files and folders first. I checked the following folder locations for any files being executed when the machine starts:
C:\Users\user1\AppData\Roaming\Microsoft\Windows\Start Menu\Programs\Startup
C:\ProgramData\Microsoft\Windows\Start Menu\Programs\StartUp
There were no files being run from the startup folders.
1. Next I checked for scheduled tasks using Splunk:
EventCode=4698 "Command"
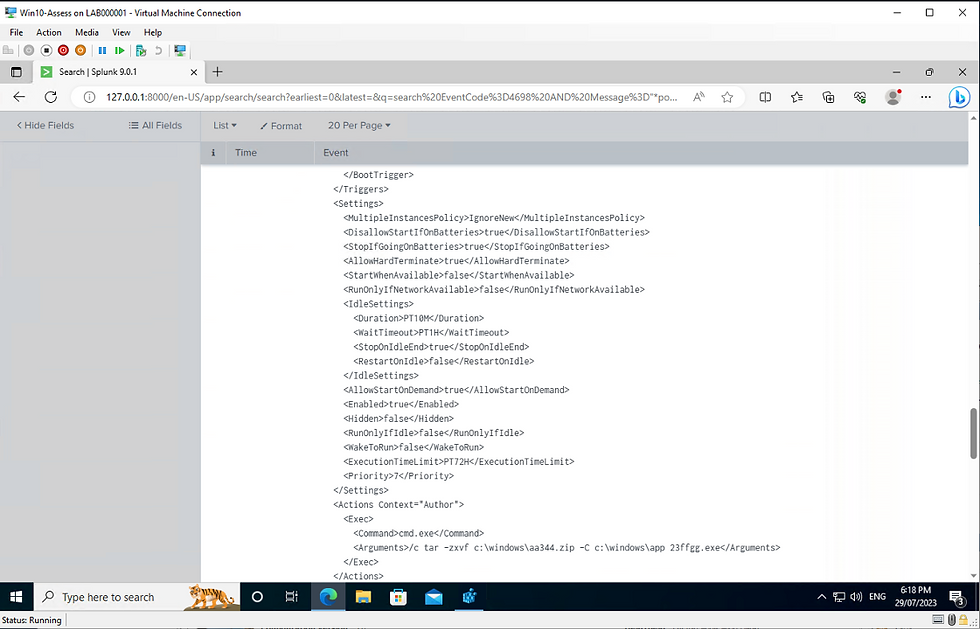
I was able to locate the malware was executing from a scheduled task. The task scheduler was running a process and unzipping a zip file from the command line and executing it with this command :
c:\windows\aa344.zip -C c:\windows\app 23ffgg.exe
Navigating back to Splunk I used the following command to search for any new processes matching the file name “23ffgg.exe”
"New_Process_Name" = "*" AND "Process_Command_Line" = "*23ffgg*.exe"
The results show a file named tar.exe being run from C:\Windows\System32\
I am not able to delete this file. I note from research that this is a bsdtar utility that reads and writes archived files and I noted that when I boot the machine a command prompt opens and closes momentarily, suggesting that something is being run on starting the machine still, but not from the startup folders.
I checked Splunk for any exploitation of the command shell and discovered evidence of cmd.exe being exploited through the use of the /Q and /c arguments. These arguments are commonly used by malware authors and threat actors.
I used the search:
EventCode=4688 AND "cmd.exe /Q /C"

I ran Task Scheduler and located a suspicious entry for “GoogleUpdate”. This scheduled task is suspicious because Google isn’t an application that is installed on the machine and its being run on Sunday evening which is unusual. I checked the task and found the instruction it is set to run the suspicious tar file from earlier.

I removed the task and rebooted the machine.
I confirmed the malicious file was not being executed any longer using Task Manager, and used Auto Runs and I checked the registry and the scheduled tasks again to make sure the malware had been removed, It had.
Whilst this was a relatively simple task it's a great way to learn how basic malware gains persistence in a system, often using scheduled tasks, auto run folders, registry keys or the malicious use of the command line or WMI.exe


